Pentest-as-a-Service (PTaaS)

We’re Certified Industry Experts





Pentest-as-a-Service
Pentest Management and Reporting... Made Easy
Real-time visibility
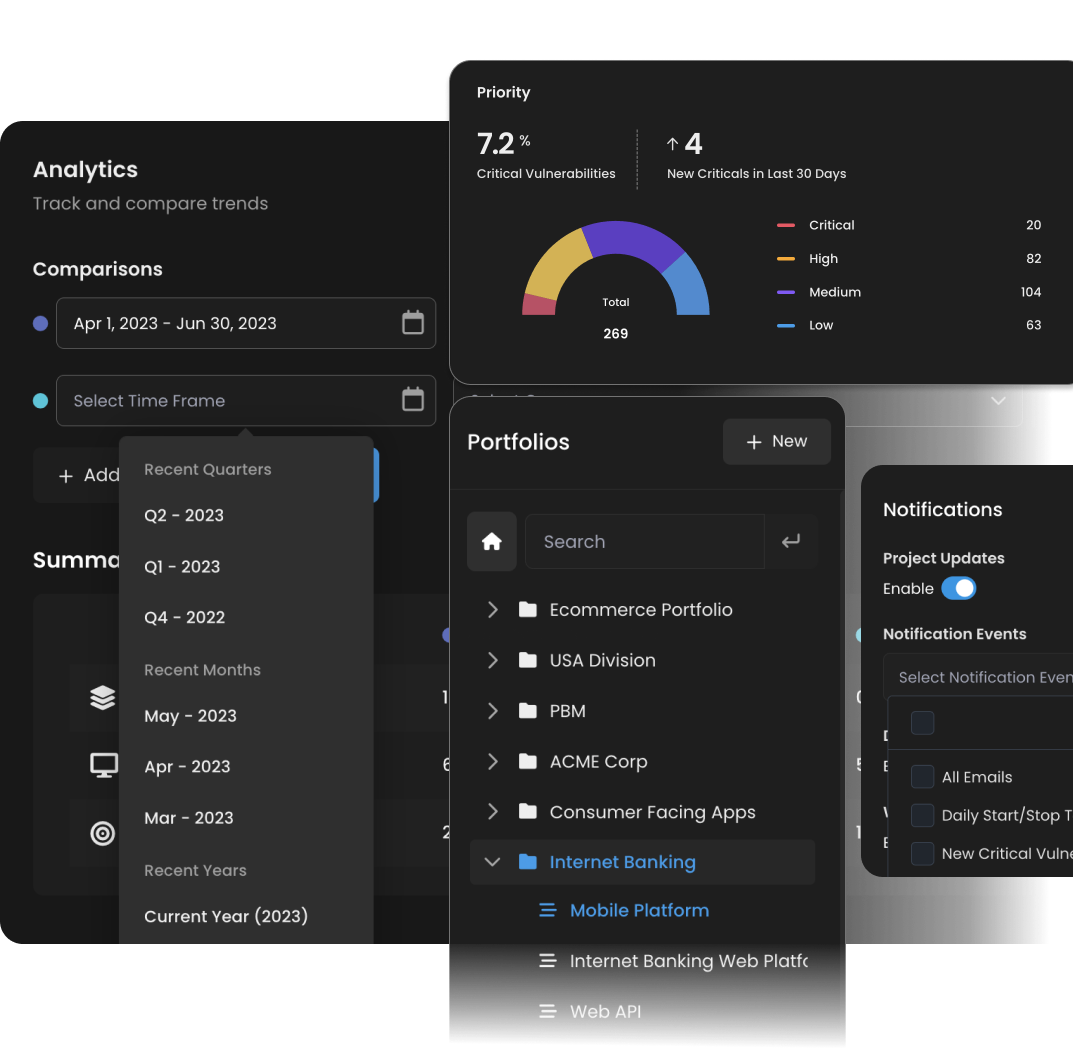
A Panoramic View of Your Attack Surface
We’ve partnered with AttackForge to deliver a modern penetration testing platform that goes far beyond static reports. Through the portal, you can collaborate directly with the pentesters performing your engagement, ask questions in real time, and gain context around findings as they are discovered.
Redline's pentest portal provides full transparency into the process, allowing you to see the exact methodology, test cases, and evidence used during testing. Instead of waiting weeks for a final report, you get continuous visibility into reconnaissance, exploitation attempts, and remediation progress. This partnership ensures every test is both a security engagement and a learning opportunity, giving your team the insight and clarity needed to respond quickly and strengthen defenses.
Continuous Visibility
Bringing stakeholders together during engagements
Our platform delivers more than reports. It gives your team a live environment to collaborate with pentesters, track vulnerabilities, and manage penetration testing from start to finish. From project creation and test execution to real-time updates and stakeholder communication, everything happens in one place. You gain complete transparency into methodology, test cases, and results, with the ability to request retesting, review findings, and monitor remediation progress as it happens.
By consolidating collaboration, reporting, and reviews into a single platform, we make penetration testing continuous instead of episodic. Security teams can launch projects quickly, perform quality reviews at scale, and maintain a clear history of every change. This continuous delivery model ensures your organization stays ahead in a dynamic threat landscape with actionable insights that improve defenses and accelerate response.


Our Playbook
Our AI Pentesting Playbook
Map System Inputs
We identify and catalog every input path including UIs, APIs, file uploads, integrations, and agent interactions. This defines how untrusted data reaches the model and highlights where injection risks exist.
Ecosystem Fingerprinting
We identify and catalog every input path including UIs, APIs, file uploads, integrations, and agent interactions. This defines how untrusted data reaches the model and highlights where injection risks exist.
Attack the Model
We evaluate the AI model for jailbreaks, safety filter bypasses, poisoning risks, inversion attacks, and configuration flaws. This ensures vulnerabilities beyond content generation are discovered and validated.
Attack the Prompt
We apply advanced prompting tactics such as context manipulation, chained instructions, hidden directives, and agent poisoning. These techniques measure how the system interprets and executes instructions under pressure.
Attack the Data
We examine training data, embeddings, and RAG pipelines for leakage, corruption, or manipulation. This identifies how poisoned or tainted data can compromise AI reliability and trustworthiness.
Application Testing
We review AI-enabled applications and integrations for traditional web security issues such as SSRF, XSS, command injection, IDOR, and insecure output handling. This ensures both classic and AI-specific vulnerabilities are addressed.
Exploit Chaining
We simulate real adversaries by chaining vulnerabilities, escalating privileges, and pivoting across SaaS, cloud, and on-prem environments. This validates the business impact of compromise beyond the initial AI layer.
Serving a Diverse Range of Industries with Expert Pentesting Services


Healthcare

Our Process
Continuous Service Delivery


Planning & Scope
Define objectives, focus areas, and engagement parameters tailored to your unique digital environment.

Discover & Assess
Employ advanced tools to identify assets, uncover vulnerabilities, and simulate real-world cyberattacks.

Report & Remediate
Deliver a clear report with actionable insights and step-by-step guidance for remediating vulnerabilities.

The Redline Difference
Results You Can Count On
Transparent Pricing
Testing that maximizes value and efficiency.
Retesting After Fixes
Ongoing validation with included retesting.
Flexible Testing
Custom scope for every environment.
Personalized Support
Access to experts when you need.
Verified
Value
Proven outcomes that justify investment.
Proven Assurance
Compliance evidence your auditors can trust.
Pentesting that delivers real results.
Actionable Reports
Expert Consultants

Frequently Asked Enterprise Security Questions
Answers to Your Questions
Yes. We provide penetration testing specifically for AI and LLM-powered applications. This includes testing for prompt injection, data leakage, model manipulation, and integration risks that traditional security assessments often miss. As AI adoption grows, specialized pentesting ensures your models and workflows remain secure and compliant.
We typically are able to schedule out within 5-10 days from a scoping call.
Pricing depends on scope and depth. Smaller, targeted assessments may start in the low five figures, while enterprise engagements scale accordingly. Factors include number of applications, network size, complexity of integrations, and whether specialized testing (e.g., AI or red team) is required.. Please reach out to us for a detailed quote. We respond to inquiries same day!
You’ll receive full access to our PTaaS portal with real-time findings, remediation tracking, and retest requests. At the end of the engagement, we deliver a technical report with detailed vulnerabilities, proof of exploitation, and remediation guidance, plus an executive summary for leadership and compliance.
We map penetration testing results to compliance frameworks such as SOC 2, PCI DSS, HIPAA, and ISO 27001. Our reports provide the evidence auditors and regulators require, and we can align testing frequency to your compliance cycles.
Scoping is based on the size, complexity, and business criticality of the systems in scope. We work with your team to understand applications, networks, cloud assets, or APIs, then define the depth of testing required. This ensures testing reflects real-world risk paths, not just surface-level scans.
Redline provides a full spectrum of cybersecurity training options. We host live webinars to share industry insights, deliver hands-on workshops for teams, and release on-demand training modules and labs that can be accessed anytime. For more interactive learning, we organize Capture the Flag (CTF) events where participants apply skills in real-world attack and defense scenarios. Whether your goal is awareness, technical depth, or team-building, our training programs are designed to strengthen skills and improve resilience.
Most one-time tests are completed in 1–3 weeks depending on scope. PTaaS clients benefit from continuous testing with real-time findings. We align timelines to your needs, whether you require a fast turnaround or an in-depth, phased approach.
Yes. Retesting is included in most engagements by default. Retesting ensures vulnerabilities have been fixed correctly and provides closure for compliance and internal risk reporting.
Redline is built by real hackers, not check-box auditors. Our team has published CVEs, climbed bug bounty leaderboards, and contributed to the security community for over a decade! We combine technical expertise with a clear reporting process that provides both deep technical insight and executive-ready summaries.
Contact Our Team
Contact Us
Global
Based in Detroit, ready to assist you globally.
Global reach, with a local touch

The Latest Blog Posts



